AWS CloudShell makes it easy to spin up a terminal right in your AWS account. Since CloudShell is just like any other terminal, you have the ability to bootstrap other tools without the need to spin up an instance.
In my last post I showed how to install Steampipe and use it to instantly query your AWS APIs using SQL right in AWS CloudShell. For example here's a query that uses the Steampipe AWS plugin to query which AWS IAM users have MFA enabled:
select
title,
create_date,
mfa_enabled
from
aws_iam_user
+-----------------+---------------------+-------------+
| title | create_date | mfa_enabled |
+-----------------+---------------------+-------------+
| pam_beesly | 2005-03-24 21:30:00 | false |
| creed_bratton | 2005-03-24 21:30:00 | true |
| stanley_hudson | 2005-03-24 21:30:00 | false |
| michael_scott | 2005-03-24 21:30:00 | false |
| dwight_schrute | 2005-03-24 21:30:00 | true |
+-----------------+---------------------+-------------+
You can simply query your environment for these type of security configuration questions using SQL. There's thousands of examples you can leverage to get you started, and a wealth of possibilities to uncover details about your AWS configurations.
Running Security and Compliance Checks
While you can explore your AWS configurations running queries, Steampipe also provides modules which are collections of related dashboards, benchmarks, queries, and controls. Steampipe mods and mod resources are defined in HCL wrapping your SQL queries to create a benchmark. There are many published mod examples to get you started with thousands of controls readily available for security, compliance, tagging, and cost controls. Published modules can be found on the Steampipe Hub, and custom mods may be shared with others from any public git repository.
For example, the AWS Compliance Mod layers benchmarks and controls covering 13 compliance standards including CIS, HIPAA, NIST, PCI, FedRAMP, SOC 2 and more. Each benchmark includes a set of pass/fail controls. Each control tests for a compliance recommendation such as "EC2 instances" should be managed by AWS Systems Manager" and reports OK or Alarm.
Here's how to run the NIST 800-53 benchmark:
If you've already completed steps 1 - 3, skip to step 4:
1. Install Steampipe
sudo /bin/sh -c "$(curl -fsSL https://raw.githubusercontent.com/turbot/steampipe/main/install.sh)"
2. Install the AWS plugin
steampipe plugin install aws
3. Install the AWS Compliance Mod
git clone https://github.com/turbot/steampipe-mod-aws-compliance
cd steampipe-mod-aws-compliance
4. Run the NIST 800-53 benchmark:
steampipe check benchmark.nist_800_53_rev_4
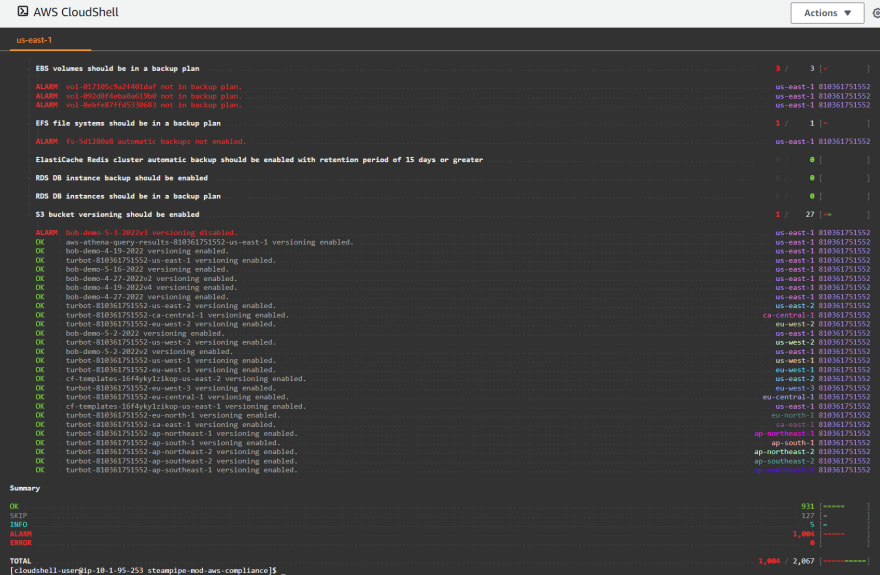
There are over 370 controls in that benchmark, so the command produces many screenfuls of output, here's the last one:
Export and Review the Findings
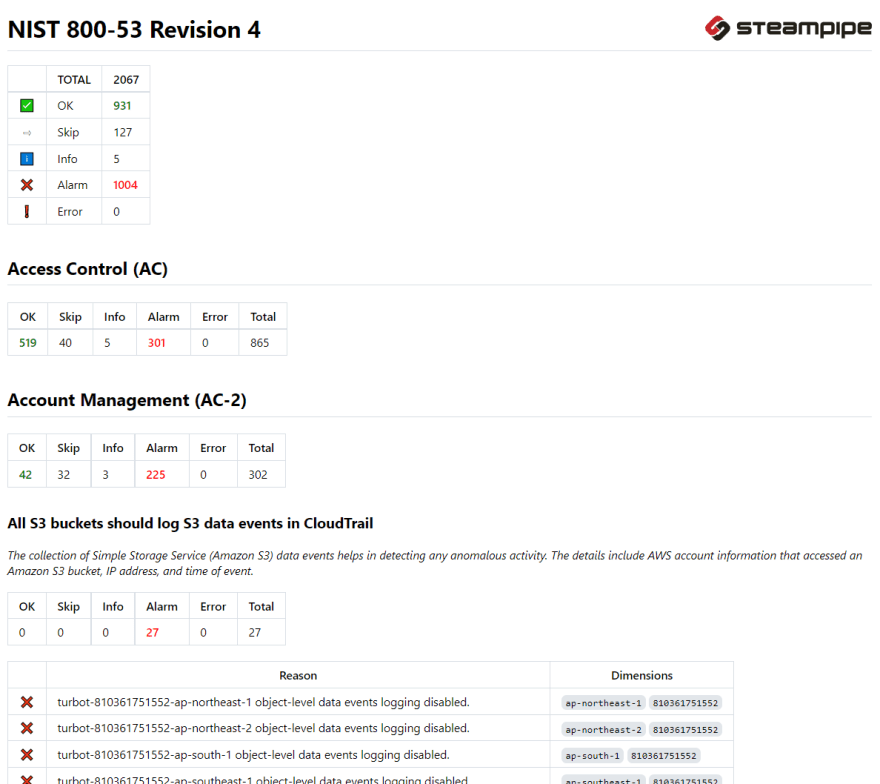
The summary is helpful, but you may want to digest the full report in varying formats. You can export to CSV, Markdown, HTML. Example of an HTML format:
steampipe check benchmark.nist_800_53_rev_4 --export=output.html
Using Files -> Download File in AWS CloudShell's Actions menu, you can download your output file steampipe-mod-aws-compliance/output.html and work with it locally.
Here's what the HTML report looks like:
AWS Compliance Quick Start
We put together a quick start script to bootstrap the flow above and prompt the user to select from the 13 available compliance benchmarks.
To get started with the quick start, spin up a new CloudShell and install Steampipe:
sudo /bin/sh -c "$(curl -fsSL https://raw.githubusercontent.com/turbot/steampipe/main/install.sh)"
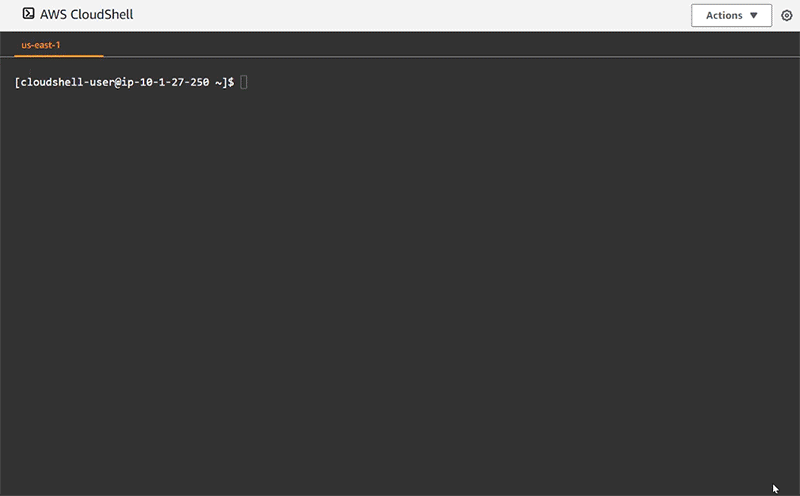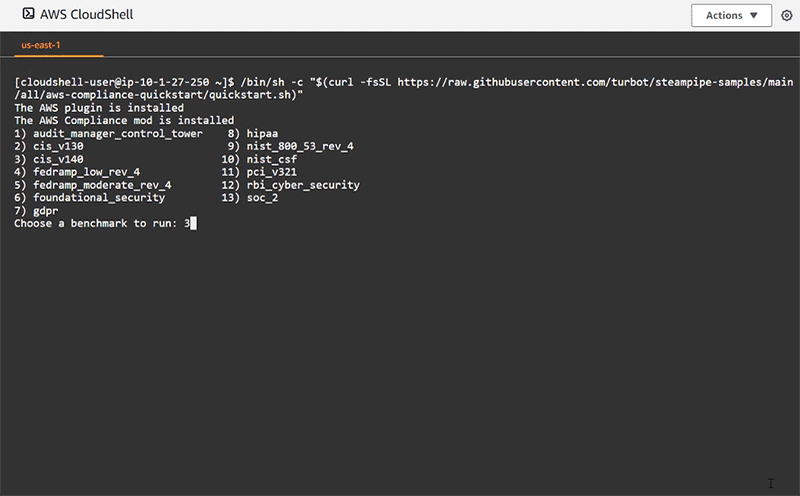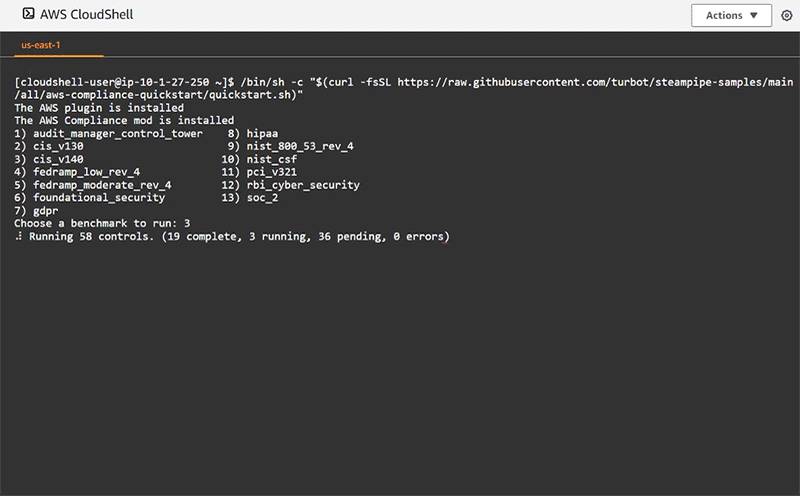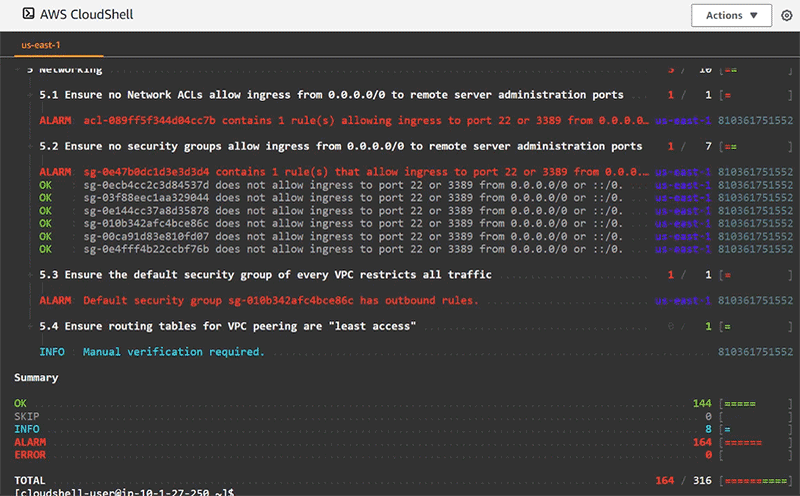
Then bring down the Steampipe AWS Compliance Quick Start script to install the AWS Plugin, AWS Compliance Mod, and receive the selection prompt asking which benchmark to run:
/bin/sh -c "$(curl -fsSL https://raw.githubusercontent.com/turbot/steampipe-samples/main/all/aws-compliance-quickstart/quickstart.sh)"
You can always run the last command again and it will skip the setup steps and prompt you for another compliance benchmark to run. Note: This last script was just a fun sample, generally you should stick to the official AWS Compliance Mod Controls to evaluate the controls, definitions and up to date information on available benchmarks.
Final Thoughts
I really enjoy using AWS CloudShell for these type of quick win use cases within an AWS account. It's remarkably easy to install your CLI tools like Steampipe, with no configuration required and instant gratification! Let me know how you use AWS CloudShell with your favorite CLI tools in the comments below.






Top comments (3)
I've gotta use SteamPipe, but I did use Prowler.
dev.to/kcdchennai/using-prowler-to...
Good to have many tools in the toolbox for assessing your cloud environments, Prowler is a great one to leverage as well!
Interested to hear how you go with Steampipe for AWS and other plugins (hub.steampipe.io/plugins). A lot of different mods to take advantage of that come packed with 1000s of controls and 100s of dashboards across AWS, Terraform, Kubernetes, and other cloud services (hub.steampipe.io/mods). Look forward to seeing what you build 🚀
Oh boy this seems so cool it's like a handy box, let me check them out!